

March 10, 2020
Over the past year or so, Google has been gradually introducing a new security feature that helps users avoid compromised passwords. This issue has very little to do with Rumpus, but as a server administrator, you may have users encounter a 'Change Your Password' security warning. It can be a little unnerving for users, so here is an overview of what is happening so that you can explain what is going on.
The warning will look something like this:
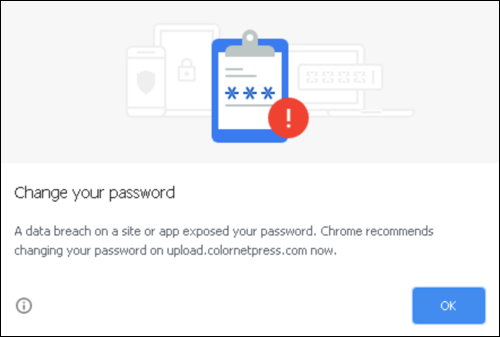
Here is my understanding of the feature:
The username and password are checked against a Google database of username and password combinations that are known to have been compromised.
This feature does not take into consideration the Web site or URL being accessed, only the name and password.
If a username/password combination have ever been marked as compromised on any site, anywhere on the Internet, the feature will display the warning.
The username/password combination will cause the warning to be displayed on any and all password protected Web sites the user visits.
One of the issues Google is targeting with this feature is the fact that username/password pairs are very commonly used by people on multiple Web sites. Many people have one (or a few) username/password pairs that they use on multiple sites, and this practice is a significant problem because if a data breach occurs on one site, the name/password is essentially compromised on all sites that person uses. For both you and your users, it is always best to use different username/password pairs on each Internet service you access.
So, if a user sees this warning when accessing your server, it means that the username/password combination has been identified as having been compromised on some Internet site. It does not mean that a data breach has occurred on your server. It means that somewhere, a breach occurred and that username and password combination was detected as being vulnerable in that breach.
The simple first step is to change the user's password in Rumpus, using the usual "User Account" window in either the Rumpus application or the Web admin interface. As always, select a strong, randomly generated password to avoid similar match failures in the future.
Note that this Google Chrome feature is likely to detect common usernames and passwords. For example, a user called "TestUser" with a password of "1234" is virtually guaranteed to trigger the change password warning, while a truly random, non-trivial password should very, very rarely cause a detection. For this reason, if a user sees this warning, it may be an indication that they are not using strong enough passwords. Please be sure to explain how important non-trivial, randomly generated passwords are to everyone's on-line security.
Also, if you haven't already, consider enabling the Rumpus feature that allows users to change their own passwords. Rumpus even includes features that allow you to require that users change passwords on a regular basis, which may be appropriate depending on your server's security needs. These features can be found on the Web Settings window, Authentication tab in the Rumpus control application.
This warning does not indicate a problem with your server, nor does it indicate that any sort of data breach or other potentially harmful activity has occurred on your server. What it means is that the username and password being used to access your server has been detected as having been compromised in some past breach, somewhere else on the Internet. To eliminate the warning, change the user's password to a non-trivial, randomly assigned string of digits, or ask the user to change their password using the Rumpus built-in function to do so. Also, use this warning to identify usernames and passwords that are perhaps not as strong as they should be, and explain to the person the importance of strong passwords.
As always, if you have additional questions or concerns about this or any other security issue in Rumpus, please contact us at support@maxum.com and we'll do our best to offer guidance specific to your server or requirements.